Cybercriminals have injected more than 15,000 malicious packages containing phishing links into the NPM repository, creating a dangerous environment for unsuspecting users.
Updated Fri, April 14, 2023 at 5:29 AM EDT
In a brazen attack on the open-source community, nearly 15,000 spam packages have clogged up the npm repository to spread malicious phishing links. "The packages were created using automated processes, with project descriptions and auto-generated names that closely resembled one another," Checkmarx researcher Yehuda Gelb said in a Tuesday report. "The attackers referred to retail websites using referral IDs, thus profiting from the referral rewards they earned." This modus operandi poisons the registry with malicious packages that contain links to phishing efforts in their README.md files, much like what software supply chain security uncovered back in December 2022.
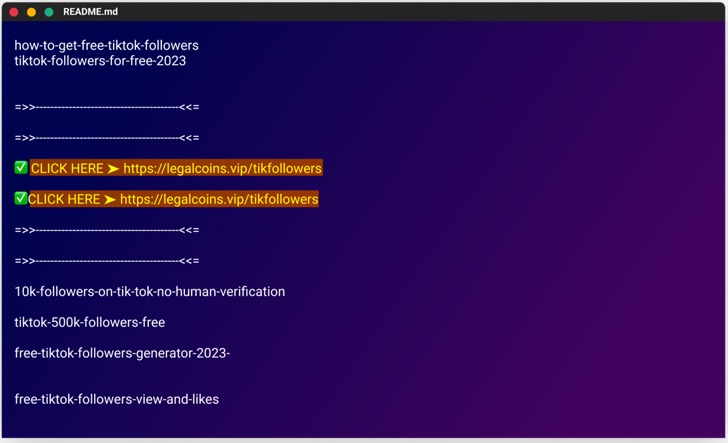
The malicious modules posed as beneficial cheats and gratis supplies, with some bundles entitled "free-tiktok-followers," "free-xbox-codes," and "instagram-followers-free." The ultimate mission of the operation is to beguile users into downloading these packages and clicking on links that lead to phishing sites where they can get false guarantees of amplified followers on social media. "The deceptive web pages are well-designed and, in some cases, even include fake interactive chats that appear to show users receiving the game cheats or followers they were promised," Gelb explained.
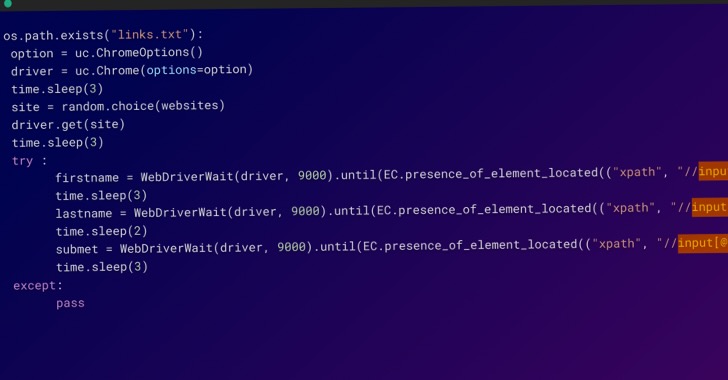
Cybercriminals are coaxing victims to complete surveys, which then open the door for even further ones or redirect them to legitimate e-commerce websites such as AliExpress. Surprisingly, these malicious packages were uploaded from multiple user accounts in a matter of hours between February 20th and 21st with an automated Python script on npm.In addition, the Python script is designed to add links of published npm packages on WordPress websites operated by the threat actor that allegedly offer Family Island cheats. To achieve this, it uses selenium package for Python to interact with these websites and make necessary modifications.
Automation was an integral factor in the success of this attack, as it enabled the adversary to rapidly publish a substantial number of packages within a concise timeframe - not to mention setting up multiple user accounts for evasion tactics. "This shows the sophistication and determination of these attackers, who were willing to invest significant resources in order to carry out this campaign," Gelb said. The findings once again demonstrate the challenges in securing the software supply chain, as threat actors continue to adapt with "new and unexpected techniques."
Updated Fri, April 14, 2023 at 5:28 AM EDT
Updated Fri, April 14, 2023 at 5:28 AM EDT
Updated Fri, April 14, 2023 at 5:27 AM EDT
Updated Fri, April 14, 2023 at 5:27 AM EDT
Updated Fri, April 14, 2023 at 5:43 AM EDT
Updated Mon, February 20, 2023 at 8:12 AM EST
Updated Mon, January 30, 2023 at 1:30 PM EST
Updated Mon, January 30, 2023 at 1:27 PM EST
Updated Mon, January 30, 2023 at 1:23 PM EST

















